Schedule Your Consultation Today!
Build Your Next Project With Industry Experts
Leverage cutting-edge technology and proven expertise to transform your business.
All information you provide will remain confidential.
Years Of Experience
Vetted Developers
Solutions Delivered
Countries Served
The custodial model isn't just about holding keys, it's about becoming the fiduciary layer between traditional finance and programmable value. We engineer custodial wallet architecture for organizations that must balance regulatory obligations, counterparty risk, and operational velocity in a landscape where trust is quantified through cryptographic proofs and audit trails.
Our work spans digital asset exchanges managing institutional order flow, fintech platforms enabling retail crypto access, and enterprises tokenizing real-world assets under regulatory frameworks. We've built the underlying custody infrastructure that keeps private keys isolated within hardware security modules, implements policy-driven transaction controls, and maintains forensic-grade audit logs that satisfy both internal compliance and external regulators.
This isn't speculative technology. It's production infrastructure supporting live capital flows, regulatory filings, and fiduciary responsibilities that demand five-nines uptime and zero-tolerance security postures.

Powering secure, self-custodial digital asset management across every major blockchain.
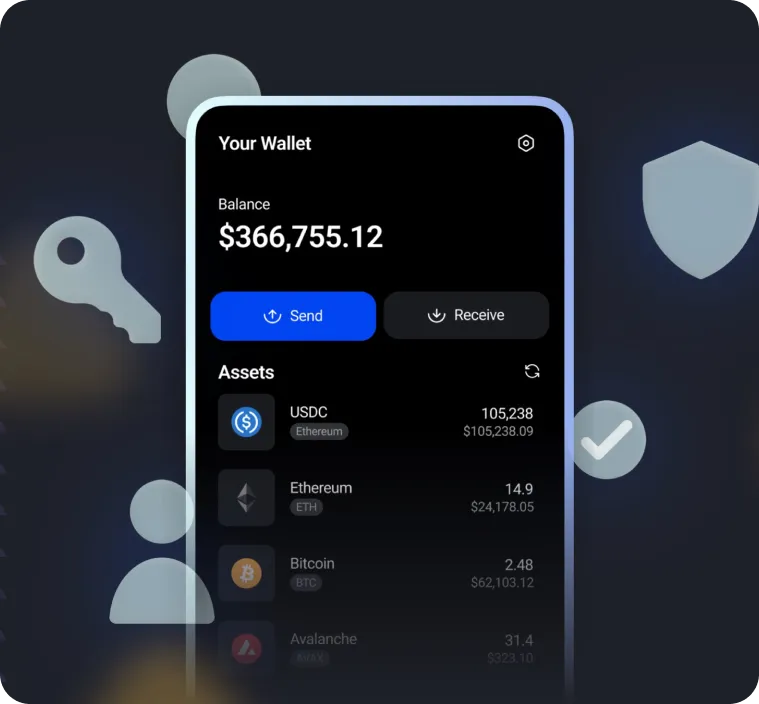
Empower users with full control over their assets while enabling seamless decentralized trading.
Automate approvals, asset routing, and trading flows through secure contract-driven operations.
Distributed key-signing architecture engineered for institutional-grade decentralized security.
Multi-party approval systems aligned with decentralized governance models and fund controls.
Gasless UX, social recovery, and programmable smart accounts that eliminate private key friction.
Real-time threat detection and automated DeFi optimization powered by machine learning.
Unified support for Bitcoin, Ethereum, Solana, Layer-2s, and multi-network asset transfers.
Direct access to lending, swapping, bridging, staking, and yield generation from one interface.
Manage tokenized stocks, real estate, commodities, and RWAs with integrated compliance workflows.
Fast, secure, biometric-enabled apps designed to feel like Web2 while functioning on Web3 rails.
Launch your own branded decentralized wallet with customizable modules and rapid deployment.
Add secure wallet functionality via API without building blockchain infrastructure internally.

Production-ready foundations that compress months of security engineering into weeks
Key management isn't your product differentiator. Neither is blockchain node synchronization or transaction construction. These are solved infrastructure problems that every custodial platform needs but shouldn't rebuild.
We provide the custody layer—tested, audited, and running in production environments. Your team focuses on the user journey, business logic, and market positioning that actually matter to your success.


Distributed key generation using threshold cryptography instead of centralized storage vulnerabilities

Account infrastructure supporting both traditional key pairs and programmable smart accounts depending on use case

Transaction signing that works across multiple signature schemes and blockchain architectures through unified interfaces

Compliance monitoring catching sanctioned addresses and suspicious patterns before transactions reach networks
The difference between launching in quarters versus years often comes down to starting with proven infrastructure instead of custom building commodity components.
The infrastructure layer between user intent and blockchain execution

Private key material is split across multiple secure locations—signing requires distributed approval without ever reconstructing a full key.

Deploy programmable smart accounts with recovery logic, spending rules, role permissions, and upgrade pathways built directly into contract wallets.

Native WebAuthn, Face ID, fingerprint security, and device secure-enclave authorization—no passwords or seed phrases required.

Users sign transactions without holding gas tokens—fees are sponsored, batched, or redirected through meta-transaction systems.

Designated guardians or institutional recovery workflows restore access using cryptographic proofs—never revealing underlying key shards.

Temporary signing access for integrated apps with preset spending caps, usage limits, and automatic expiration rules enforced on-chain.

User intents are converted into optimized multi-step transactions across protocols, executed atomically without exposing underlying complexity.

Synchronized balance, history, and state tracking across Bitcoin, Ethereum, L2s, and multi-chain ecosystems through normalized data models.

Machine learning patterns detect anomalous actions, suspicious routing, or unusual velocity before a transaction reaches the chain.

Geographic restrictions, tiered approvals, velocity limits, and custom security policies enforced directly at protocol or contract level.

Zero-knowledge proof systems confirm compliance or identity requirements without exposing personally identifiable information.

Add hardware key validation, multi-party approval flows, time-locked protections, or extra signing layers as your risk model evolves.
Why holding keys creates business value beyond transaction fees

Biometric login converts users who would otherwise abandon onboarding when prompted for seed phrase backup.

Institutional-grade recovery workflows reduce support requests linked to lost keys or inaccessible wallets.

Optimized hot wallet systems allow sub-second withdrawals without compromising user experience or system safety.

A centralized custody core supports thousands of users efficiently through shared, optimized infrastructure.

Security systems designed to meet underwriting standards enable access to digital asset insurance policies.

A clear custodian framework simplifies compliance and removes ambiguity found in decentralized access models.
From requirements to production deployment
Map user expectations, regulatory obligations, and operational constraints that shape the custodial architecture.
Define key generation processes, threshold signing parameters, cryptographic backup flows, and secure signing protocols.
Integrate identity verification, risk scoring, transaction monitoring, and automated reporting requirements into custody operations.
Develop distributed signing services, blockchain connectivity, smart account systems, and enforcement engines for custody policies.
Conduct external audits of cryptographic systems, key isolation layers, access policies, and infrastructure hardening.
Deploy with full observability including signing latency, transaction success metrics, and anomaly detection systems.


Deploy within your own security boundary with complete operational control over your custody architecture.








We've been the technology backbone for startups and enterprises alike, driving innovation at every scale.






























Our partnerships with hardware security manufacturers, blockchain infrastructure providers, and compliance platforms aren't marketing relationships. They're technical integrations expanding what's possible in regulated custody environments.
These collaborations deliver solutions meeting institutional security requirements while maintaining the operational velocity competitive markets demand.



Custody enables account recovery, biometric authentication, and instant access without seed phrases or hardware wallets.
You trade some liability for higher conversion rates and better user retention. The right model depends on your users and business economics.














Partner with our experts and turn your visionary ideas into scalable, market-leading solutions

Dubai

Brussels

Tirana

Muscat

Abu Dhabi

Budapest

Milan